Typical scenario would probably be: you visited a website and you clicked some links (either you've been teased or you really wanted to go there), then the harmful script run that caused your browser to be redirected to some malicious websites.
So if you're the bad ass hacker, where do you want to implant those malicious scripts/codes that would lead to virus infection? Good candidates would be those popular sites such as social networking sites (friendster, myspace, etc), or the likes of youtube, digg, and other very popular sites. Then that guy would do his trick to persuade you on clicking his malicious link (unless hes got new technique (i mean, new
vulnerability probably, or any way to
exploit some security loopholes) how to download and execute his program to user's pc automagically =)).
Take a look on this example of an entry on digg:

Its "Eva Longoria sex tape" That would be very tempting to check out isn't it? =P Now, the bad ass will post a comment specifying the link for the video. And because you're excited to see it (who wouldn't?), you clicked the link and the browser will of course drive you to the destination.
But the website (supposedly hosting the sex video) displayed some (fake) error message and would want you to install something to correct the error. Needless to say that the program it offered you to download and install is most likely a malicious software. Its usually a small program that when run, would download another (malicious) program, and the infection proceeds.
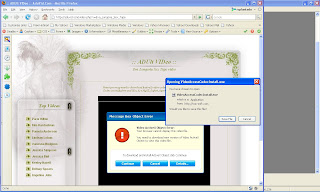
Because of some security measures from web browsers, automatic download and execute are now commonly prevented. Bad hacker must find a way (some sort of new vulnerability) to do the automatic download and execute from web browser. Otherwise, all they can do is to trick the user to download and run their code. In other words,
don't run any program from untrusted source!
If your antivirus software didnt catch it, just send it to online virus scanners like
virustotal or
virusscan. Some AV products might have already detection for it:
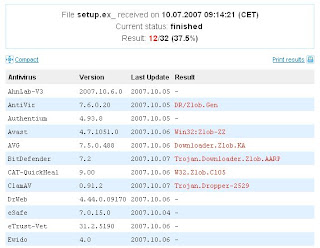
If you're curious what the f$%k is it doing, check their website for virus description. If no analysis for it yet, send it to
sunbelt's malware analyzer. Thanks to sunbelt for its wonderful free service that would save some precious time analyzing some malware. In fact, I've sent the sample to sunbelt and the complete analysis can be found
here.

Unless you have free time to dissect it by your own for curiosity, you can check
my previous post on tools that could help you reverse engineer a malware.
Clearly, when you check the
sunbelt's analysis for its activities, it's a malicious program that downloads another programs (could be another virus or worms) from a remote websites, executes it to the PC, modifies some registries to run everytime , drop other components and so on so forth - typical malware behavior.









.jpg)
.jpg)